You sometimes would see somebody doing something cool with SSH(Secure Shell), like without password, or even without key, or even more, port forwarding to break the firewall restrictions.
This post will discuss ssh tricks of authentications methods and port forwarding approaches.
Three kinds of SSH authentication methods:
- Password
- Public/private key pair
- Host-based authentication
There are three kinds of SSH Forwarding:
- Local Port Forwarding
- Remote Reverse Forwarding
- Dynamic Port Forwarding
This post will make these stuff more clear.
1. SSH Authentication Methods
We won’t talk about the password methods since it’s too easy.
1.1. Public/Private Keypair, free password
- Step 1: Genrate Keys by typing
ssh-keygenfrom youserver1.- It will generate
~/.ssh/id_rsaand~/.ssh/id_rsa.pubkey pairs which are private key/public keys of yourserver1of the user whom you’re currently logged as. - private key should be kept secret
- public key is meant to be shared
- It will generate
- Step 2: Copy the content of public key to
remoteserver’s~/.ssh/authorized_keys, by appending this file. - Step 3: Login from
server1toremoteserver, you don’t need password now!
1.2. Host-based Authentication
- Doesn’t need user credentials(password or key), actually we just write it in a configuration file, it’s kind of alias
- Provides trust based on hostname and userid
- Userid on both system has to be the same
Here is an example that login into server1 vagrant box:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50# Here we list the hostname and its config
[09:51 PM morganwu@morgan-yinnut ~]$ cat ~/.ssh/config |grep -A6 srv1
Host srv1
User vagrant
Port 2222
Hostname 127.0.0.1
IdentityFile /Users/morganwu/Developer/workspace/ssh_port_forward/server1/.vagrant/machines/default/virtualbox/private_key
StrictHostKeyChecking no
# Here we just ssh with an alias without username and hostname
[09:51 PM morganwu@morgan-yinnut ~]$ ssh srv1
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
IT IS POSSIBLE THAT SOMEONE IS DOING SOMETHING NASTY!
Someone could be eavesdropping on you right now (man-in-the-middle attack)!
It is also possible that a host key has just been changed.
The fingerprint for the ECDSA key sent by the remote host is
SHA256:jYEhZ8yXtOJFowmQnMyA+bHshrhX7H30vVQF9UyND48.
Please contact your system administrator.
Add correct host key in /Users/morganwu/.ssh/known_hosts to get rid of this message.
Offending ECDSA key in /Users/morganwu/.ssh/known_hosts:247
Password authentication is disabled to avoid man-in-the-middle attacks.
Keyboard-interactive authentication is disabled to avoid man-in-the-middle attacks.
Welcome to Ubuntu 14.04.5 LTS (GNU/Linux 3.13.0-112-generic x86_64)
* Documentation: https://help.ubuntu.com/
System information as of Fri May 19 01:50:52 UTC 2017
System load: 0.28 Processes: 78
Usage of /: 3.6% of 39.34GB Users logged in: 0
Memory usage: 25% IP address for eth0: 10.0.2.15
Swap usage: 0%
Graph this data and manage this system at:
https://landscape.canonical.com/
Get cloud support with Ubuntu Advantage Cloud Guest:
http://www.ubuntu.com/business/services/cloud
0 packages can be updated.
0 updates are security updates.
New release '16.04.2 LTS' available.
Run 'do-release-upgrade' to upgrade to it.
Last login: Fri May 19 01:50:53 2017 from 10.0.2.2
vagrant@vagrant-ubuntu-trusty-64:~$
2. SSH Forwarding
2.1. SSH Local Normal Port Forwarding
Here is the scenario why we need Port Forwarding: bypass the private network, or using the Jumpbox.
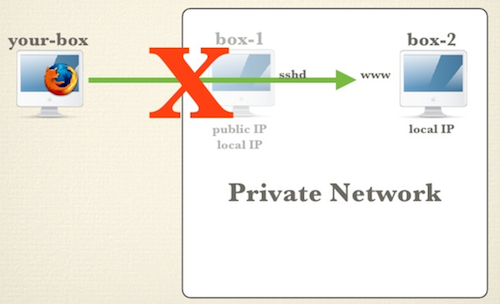
Now we want to access web server on box2 via box1. Here is how we create a local port forward.
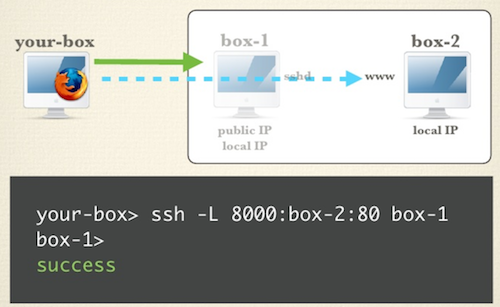
Now we can type localhost:8000 from your-box, this will forward the request to box-2:80 via box-1 ssh tunnel created above!
If we have multiple box-2 here, this is the load balancing model.
We call this as local port forwarding instead of remote port forwarding, since the setup direction is the same as the resource access direction. This is also called the normal tunnel instead of the reverse tunnel via ssh. This can be done by following three steps:
- setup ssh connection from
your-boxtobox-1 box-1forward the requets tobox-2- so you can access
box-2fromyour-boxnow evenbox-2is in the internal network
Run the command ssh -L localport:DEST_HOST:DEST_PORT VIA_HOST locally and then access local localport to get the DEST_HOST:DEST_PORT content.
This will open a localport listened locally, to serve all requests from local and then forward them to DEST_HOST:DEST_PORT by using the ssh tunnel from local to the VIA_HOST.
2.1.1. Share Your SSH Local Forwarding
We could enable localport to be accessed by other machines by appending the -g switch.
Next we enable local port forwarding from localhost:8000 to ece.uwaterloo.ca:80 via ecelinux4.uwaterloo.ca:22
1 | [11:23 PM morganwu@morgan-yinnut proxies]$ ssh -L 8000:ece.uwaterloo.ca:80 -g m92wu@ecelinux4.uwaterloo.ca |
Here lists the port information, we can see 8080 is bound to all inet interfaces.
1 | [11:23 PM morganwu@morgan-yinnut proxies]$ netstat -na|grep tcp|grep 8000 |
Now let’s access the ece.uwaterloo.ca:80 page from another private virtual machine on my local computer. We can see it could have access to that page now.
1 | vagrant@vagrant-ubuntu-trusty-64:~$ curl 192.168.0.12:8000 |
Here is an image for demonstrating this:
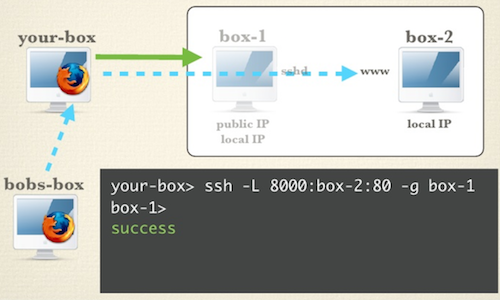
2.1.2. Use Compression via this tunnel
By using -C together with -L option.
2.2. SSH Remote Reverse Port Forwarding
Local Port Forwarding has the same direction of SSH tunnel as the request forwarding, while Remote Reverse Forwarding does the opposite direction.
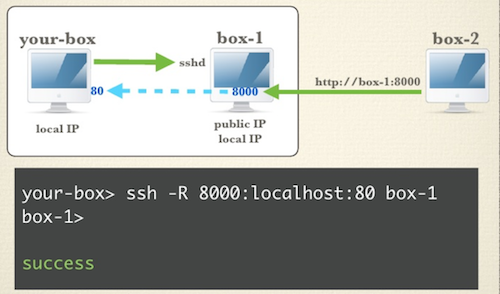
So you setup a ssh tunnel from your-box to box-1 which has a public address while your-box doesn’t. But you would like to access your-box from box-2 which is outside. Now you can only do this via box-1.
If we have multiple your-box here, this is the so-called reverse proxy load balancing model.
So our command format is ssh -R VIA_LISTEN_PORT:DEST_HOST:DEST_PORT VIA_HOST,
This command will:
- open a ssh tunnel from
DEST_HOSTtoVIA_HOST - listen a
VIA_LISTEN_PORTon theVIA_HOST - forward all requests from
VIA_HOST:VIA_LISTEN_PORTtoDEST_HOST:DEST_PORT
Also, the -C option will work here.
2.3. SSH Dynamic Port Forwarding
In the SSH-Local-Normal-Port-Forwarding, we already know we can forward localhost:8000 request to remote_server:port via a remote public server, but this is only for specific port.
What if we want to forward every kind of requests? This is the idea of dynamic port forwarding, which is also be called as a proxy.
1 | $ ssh -D 9999 -C m92wu@ecelinux4.uwaterloo.ca |
The above command will forward every requests from localhost if you setup this socks proxy as the proxy of your client.
References: